It is not always easy to securely manage access to infrastructure and production systems. Access can occur locally or remotely, and those who gain access are not always internal personnel. The Covid-19 emergency has highlighted the need for increased attention to the problem and has companies looking for hints and ideas for assessing cybersecurity aspects.
THE CONTROLLED ACCESS MANAGEMENT
Currently, companies have countless IT systems within their organizations, and both internal and often external staff manage these systems. IT infrastructure and specific systems must be accessed and managed by experienced staff, but how should we deal with this when it is not possible to use in-house staff?
Not all companies have structured IT departments with well-defined tasks. When specific skills are searched for outside of a company, more attention must be paid to those who interact with the company’s systems. Stopping production activities performed without proper attention and experience can have serious repercussions. "Trust your people, but pay attention," because when managing multiple tasks simultaneously, the likelihood of making mistakes is not very remote.
For this reason, whenever a company allows outside personnel access to its systems, it must ensure that it acts only on the necessary systems. IT systems and infrastructure represent some of the most valuable assets of companies; proper management of them must allow and authorize access only to those who are strictly necessary.
On paper, this process is easily designed, but it requires changing processes to implement it, equipping users with appropriate tools and changing the way they work.
Perimeter definition
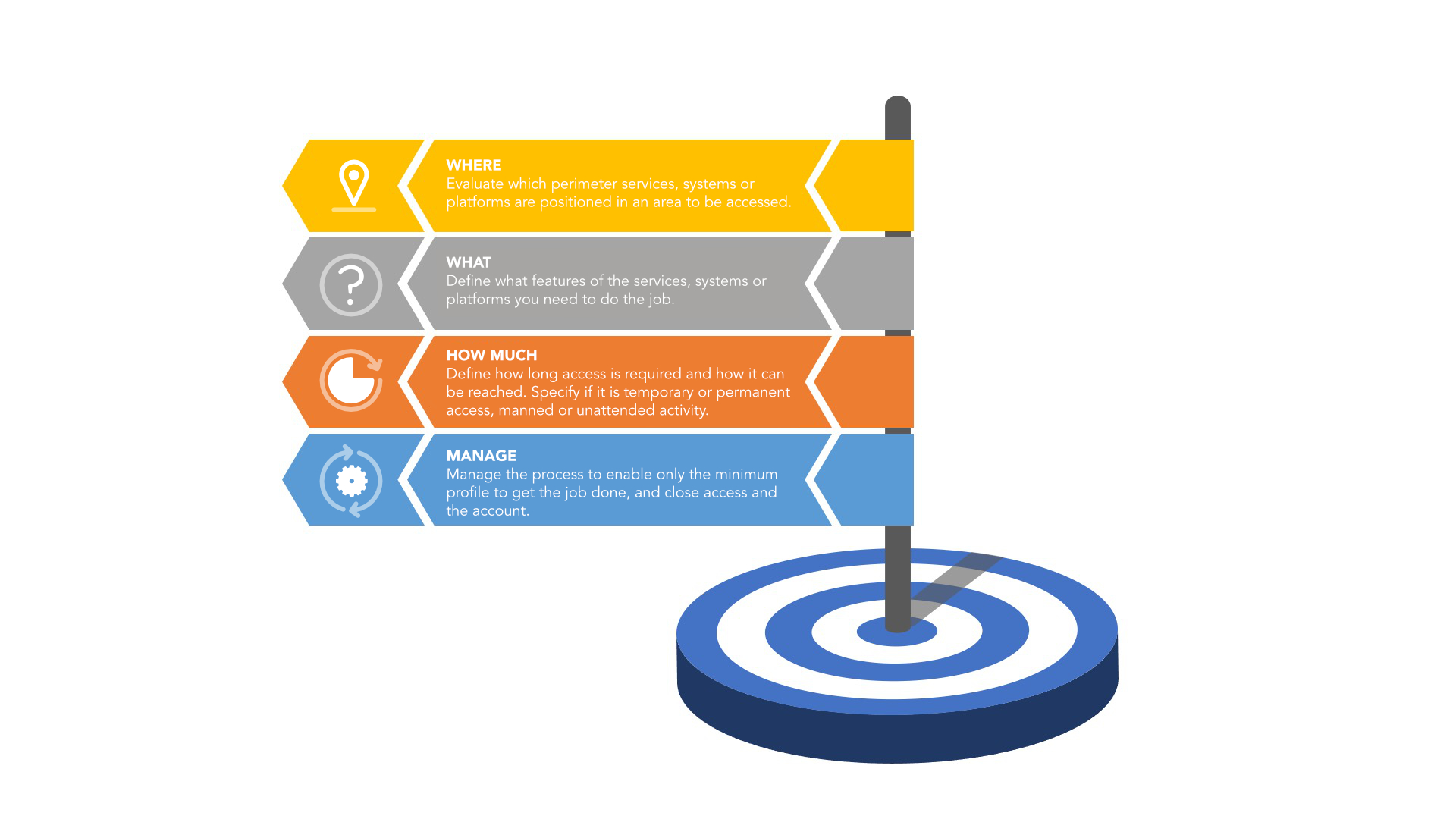
Before securing any system, it is necessary to ask a few questions. For example, ask yourself:
- On what infrastructure is a particular system hosted?
- From where should I allow access to it?
- How do I allow an initial assessment to be performed?
Access placements such as segregations become important factors and define perimeters as well as work zones.
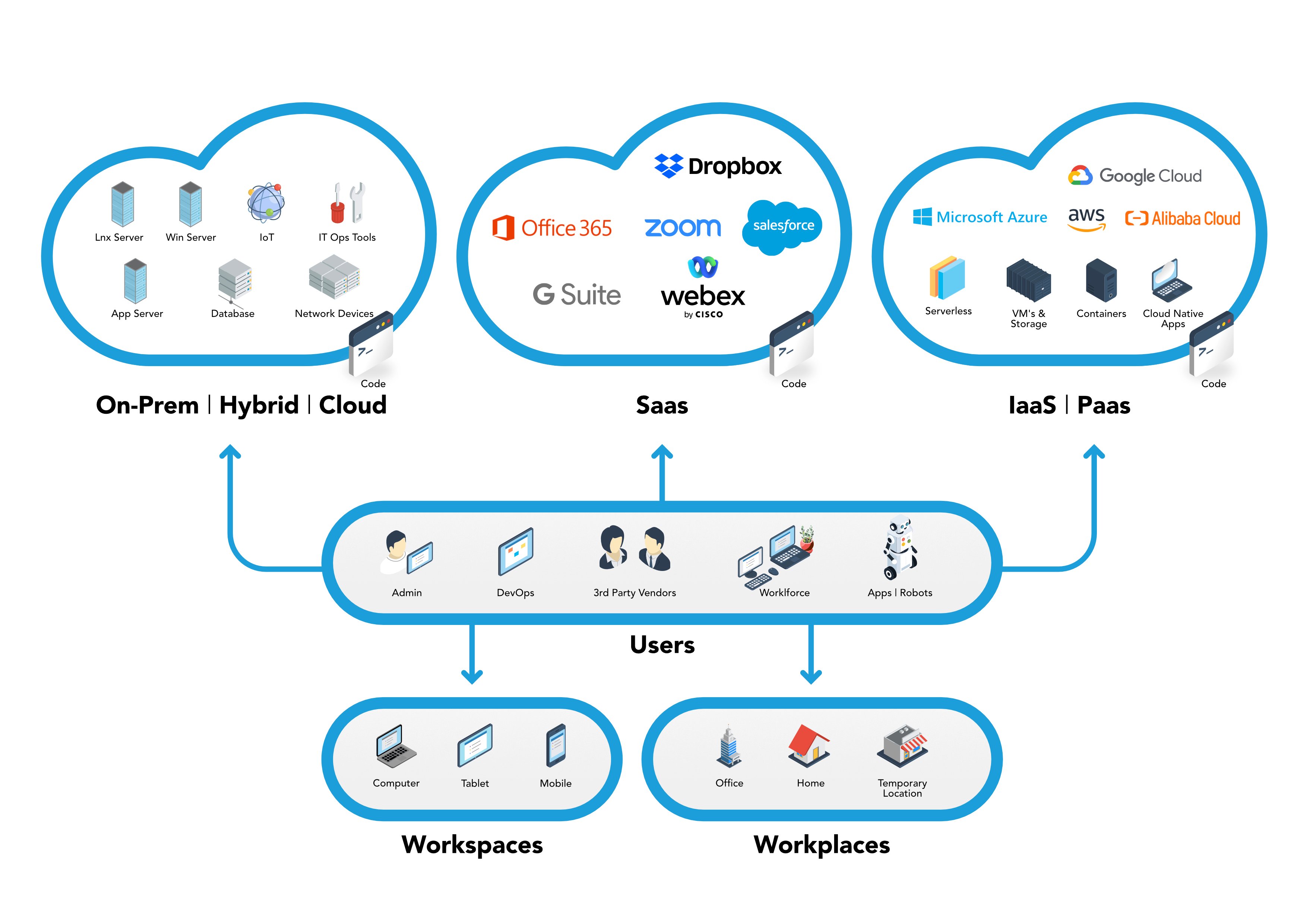
Today, IT infrastructures are becoming increasingly complex, interconnected, integrated, and in many cases are even moving outside the company's physical perimeters. IT and engineering departments have to manage a mix of different perimeters in addition to internal ones. Cloud solutions are becoming more and more prevalent, mixing with traditional work environments (workspaces) and various access platforms (workplaces).
Theoretically, if we wanted to control access to an IT infrastructure, disconnection from the Internet would be enough. We know that this approach is no longer possible and would only give a false impression of attack reduction. Attack threats do not only come from the outside, but by paying close attention, it is possible to reduce the likelihood of this occurrence and it can be mitigated.
Careless suppliers or unhappy employees can be examples of those to watch.
How to define a perimeter
A security perimeter is defined as an isolated space managed by control systems (e.g., firewalls, endpoints, etc.).
For perimeter security, security professionals must assess the risks and look for a perimeter-based approach to protect in order to mitigate threats to systems in a defined network. In fact, recommended procedures for perimeter security include threat recognition, surveillance detection, and pattern analysis to be applied.
Defining perimeters helps to better identify the areas to focus on.
Before starting to protect any asset, it is necessary to define the perimeters or zones to be controlled. The example below helps to create an initial breakdown, and dividing a problem into smaller zones allows easier and more manageable assessments to be conducted.
However, in IT security, perimeter security alone cannot be entirely effective. With perimeters, it is possible to define better rules for communication to and from other networks, but to limit the likelihood of a security failure event occurring, it is necessary to take the next step and identify what to protect.
What we need to protect
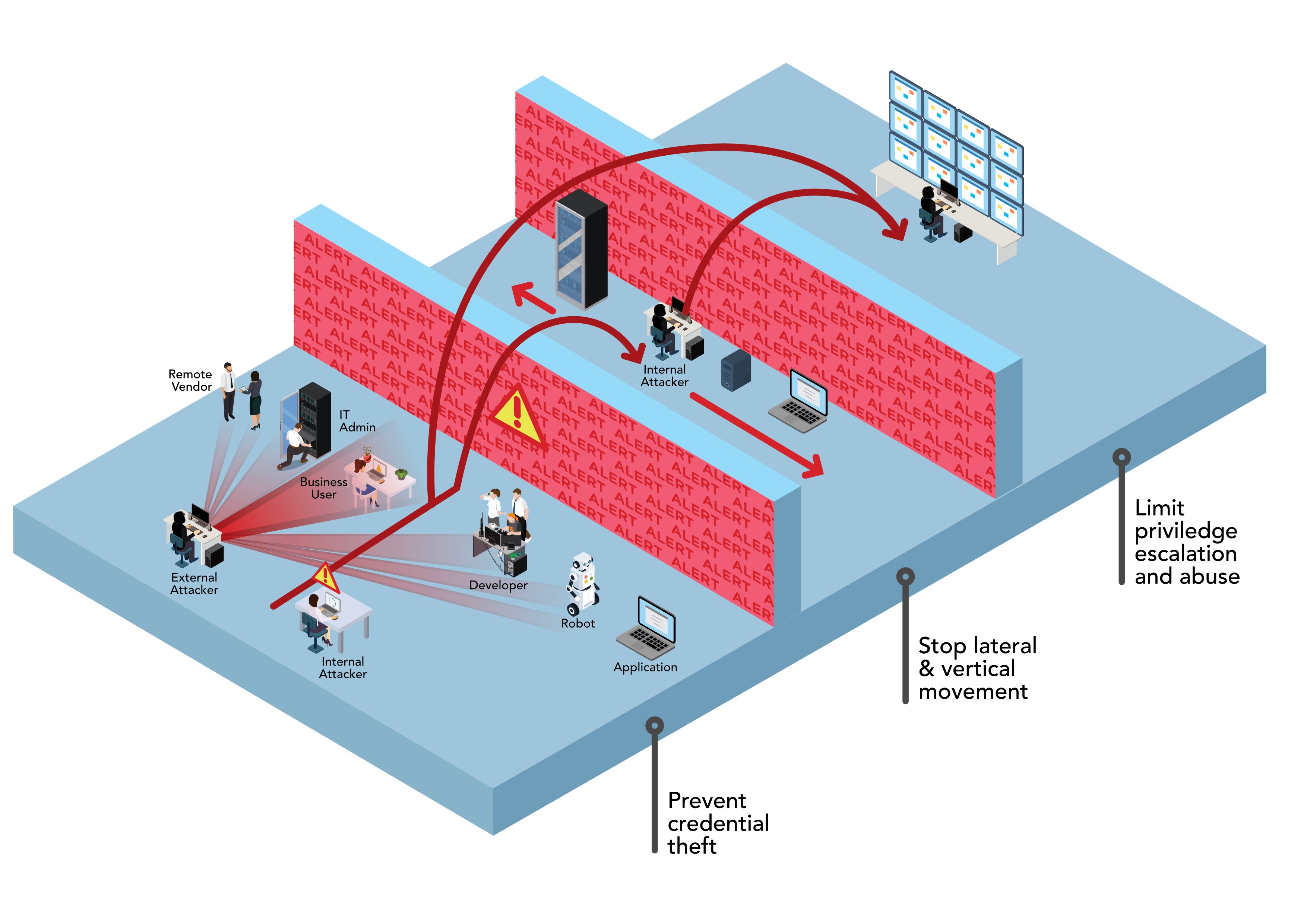
While perimeters help protect areas of access, they are not always sufficient. In fact, there are instances when stealing credentials, making lateral or vertical movements, and obtaining higher privileges undermines the model based only on perimeter management.
Following the given points, you can proceed by starting with an inventory of your systems in order to define a list that includes not only systems but also supporting services and infrastructures. The list helps to assess the potential risk to the company and to define the operational methods of access and use.
The next step is to identify identities with privileged access that can be exploited to control an entire environment (e.g., cloud or on premise). The focus on these identities must be increased if we want to reduce risk.
The most problem-conscious companies have already established best management practices; often the processes that govern them are manual. Assigning and tracking privileged profiles and managing the accounts that use or operate the systems may no longer be sufficient.
For example, without a process for managing accounts and rotating associated passwords, credentials sometimes remain unmodified for months or even years after systems are deployed. This is compounded by the use of the same common passwords for profiles (e.g., same passwords for administrative server access accounts).
The manual process would also be functional, but in the day-to-day and more frenetic work rhythms, employee, vendor and business partner accounts can often remain active for a long time. The combination of dormant accounts and service accounts that never change passwords exposes the company to possible data breaches and malicious attacks. Unhappy employees or outside attackers can exploit dormant accounts or obsolete passwords to structure sophisticated attacks.
Suggestions for good management process
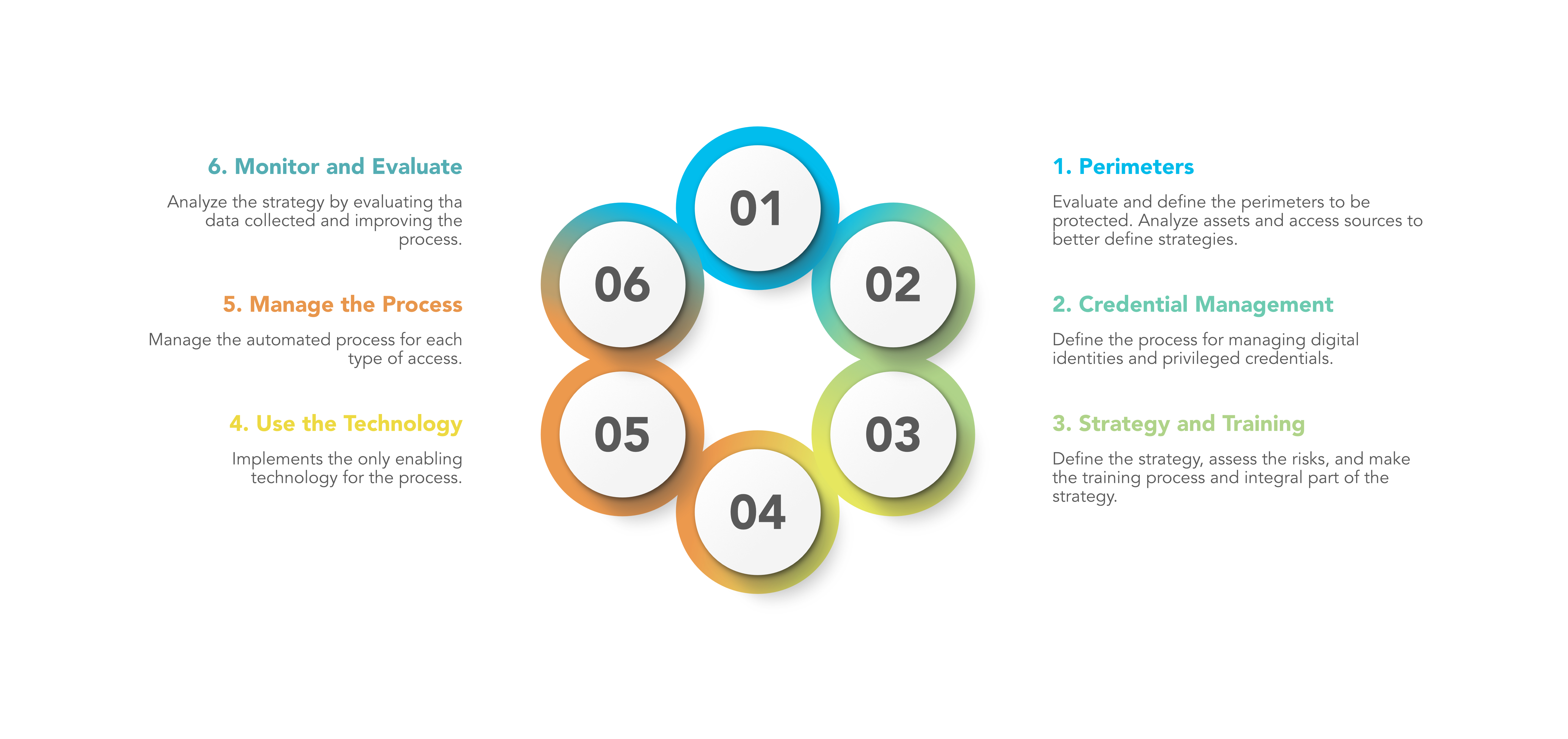
A set of different components must be mixed to define a good management process. At least six steps are suggested to be evaluated, all of which are part of an iterative model.
The diagram below best summarizes these points. The first two points were already introduced in the previous section; the others will be analyzed now.
Strategy is important to define for a structured approach for how to address common issues. Whenever access to a system must be permitted, a set of questions allow a quick, standardized assessment to be performed to reduce risk. Threats today can come from multiple sources, and being caught unprepared each time slows down activation processes. Often forgotten is the training that plays a very important role in good process management, and not making it an integral part of the strategy reduces its effectiveness or in some cases defeats the process itself.
At this point the support of technology becomes functional because manual processes are only valuable when there are relatively few elements to manage. As the number of services and perimeters to be managed increases, it is essential to have enabling tools to facilitate their management.
Tools that can help with good management can be grouped into:
- Identity Governance & Administration (IGA) - to authorize the assignment of profiles with specific capabilities, track their assignments for quality purposes, and define what enabling training must be verified prior to assignments.
- Privileged Access Management (PAM) - solutions to manage privileged access, typically including an Access Manager, a Session Manager and a Password Manager to detect and defend against security-related threats.
Controlling access sessions is also something that should not be underestimated. Access that is granted toward systems and infrastructure should be directed only to that which is strictly necessary for the purpose of performing tasks. Access cannot always be supervised or authorized every time by employees.
Vendors and remote users who typically need to access internal resources frequently should be managed with an evaluated and approved process.
Good management becomes a natural consequence when the previous steps have been carefully followed and evaluated. Finally, to complete the process, a management re-evaluation must be performed periodically. New needs or the integration of new solutions may be important to further improve one's management flow.